arpalert ...
with DHCP range exceptions, libnotify and mail alerting (based on ubuntu-linux)
1) install
aptitude install arpalert
aptitude install libnotify-bin
aptitude install postfix (MTA) # config not covered here
2) configure arpalert (/etc/arpalert/arpalert.conf)
[...]
user = root # dismiss privilege separation on your own risk (for X notify)
daemon = true # run in background/daemon mode
interface = eth0,eth1 # in my case eth1.123,eth1.456 (VLAN interfaces)
action on detect = "/var/lib/arpalert/arpalert" # see 3)
# [ change log, alert and mod config lines ]
log file = "/var/log/arpalert.log" # touch file and modify access rights
[...]
3) configure arpalert script /var/lib/arpalert/arpalert
#!/bin/bash
# handle only IPs from our nets
if [[ "$2" =~ .*192.168.* ]]; then STATUS=OK; else exit 0; fi # var $STATUS is a dummy
# DHCP exclude
for ip in {20..200}; do
if [ $2 == "192.168.1.$ip" ]; then exit 0; fi # DHCP range 192.168.1.20-200
if [ $2 == "192.168.2.$ip" ]; then exit 0; fi # DHCP range 192.168.2.20-200
done
# router mac address / more than one IP per MAC / false positives
if [ $1 == "00:08:00:11:22:33" ] && [ $5 -eq 0 ]; then exit 0; fi
# computers with virt. ip-addresses
for f in `cat /etc/arpalert/maclist.dup`; do
if [[ $f =~ .*:.* ]]; then MAC="$f"; continue; else IP="$f"; fi;
if [ $1 == $MAC ] && [ $2 == $IP ]; then exit 0; fi
done
case $5 in
0 )
AlertType="IP change";;
1 )
AlertType="MAC address already detected but not in white list";;
2 )
AlertType="MAC address in black list";;
3 )
AlertType="New MAC address";;
4 )
AlertType="Unauthorized ARP request";;
5 )
AlertType="Abusive number of ARP request detected";;
6 )
AlertType="Ethernet MAC address different from ARP MAC address";;
7 )
AlertType="Flood detected";;
8 )
AlertType="New MAC address whithout IP address";;
9 )
AlertType="MAC change";;
* )
AlertType="unknown";;
esac
# mail
MAILBODY="$(date), Intruder IP: $2, Intruder MAC: $1, IF: $4, Type of alert: $AlertType"
echo $MAILBODY | mail -s "ARP-Alert" ToMe@mydomain.tld
# libnotify
beep # make noise
export DISPLAY=:0
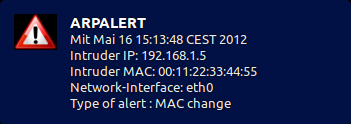
notify-send "ARPALERT" "Time: $(date) \n Intruder IP: $2 \n Intruder MAC: $1 \n Network-Interface: $4 \n Type of alert : $AlertType" -i /path/to/my/icons/alert.jpg
4) edit /etc/arpalert/maclist.allow based on your network
# hint: take data from /var/log/arpalert.log
# MAC IP INTERFACE
11:11:11:11:11:11 192.168.1.1 eth0
22:22:22:22:22:22 192.168.2.2 eth1
5) edit /etc/arpalert/maclist.dup
06:ba:ce:11:22:33 192.168.1.10 192.168.11.10
58:b0:35:11:22:33 192.168.1.14 192.168.11.14
5) start / autostart
service arpalert start
update-rc.d arpalert defaults
*) pre tests
tail -f /var/log/arpalert.log
echo "testmail" | mail -s "testsubject" ToMe@mydomain.tld # mail
notify-send "testsubject" "testbody" # libnotify
/var/lib/arpalert/arpalert 00:11:22:33:44:55 192.168.1.5 arg3 eth0 9 # arpalert script (mail and libnotify)
*) final tests / arp spoofing
arpspoof -i eth0 -t 192.168.1.1 192.168.1.5 # arpspoof [-i interface] [-t target] host
ettercat -T -M arp /192.168.1.1/ /192.168.1.5/ # Man-In-The-Middle Attack with ettercap
by Markus Sesser
